How To Use Remote IoT Behind Firewall Using Mac Server
As technology continues to evolve, the Internet of Things (IoT) has become an integral part of modern infrastructure. However, managing remote IoT devices behind firewalls can be challenging, especially when using a Mac server. In this comprehensive guide, we will explore practical methods to securely access and manage IoT devices while ensuring compliance with cybersecurity protocols.
Understanding how to use remote IoT behind a firewall using a Mac server is crucial for businesses and individuals who rely on connected devices. Firewalls are essential for protecting networks, but they can also create barriers when trying to access IoT devices remotely. This article will provide step-by-step instructions and expert insights to overcome these challenges.
This guide is designed for IT professionals, network administrators, and anyone interested in mastering the art of remote IoT management. By the end of this article, you will have the knowledge and tools necessary to securely connect to IoT devices from anywhere in the world.
- What Happened To Brodie Moss
- Naiah And Elli
- The Trench Family Zakyius
- Nicole Laeno Videos
- Ariel Camacho Birthday
Table of Contents
- Introduction to IoT
- Understanding Firewalls
- Why Use Mac Server
- Methods to Access IoT Devices
- VPN Solutions
- Port Forwarding
- Reverse SSH Tunnel
- Cloud-Based Solutions
- Security Considerations
- Best Practices
- Conclusion
Introduction to IoT
The Internet of Things (IoT) refers to the network of physical devices embedded with sensors, software, and connectivity, enabling them to exchange data. These devices range from simple household gadgets to complex industrial machines. The growth of IoT has revolutionized industries, improving efficiency and providing real-time insights.
However, as IoT devices become more prevalent, managing them remotely presents unique challenges. One of the primary obstacles is accessing these devices behind firewalls. A firewall acts as a barrier between trusted and untrusted networks, making it difficult to establish secure connections to IoT devices from external locations.
In this section, we will explore the basics of IoT and why remote access is critical for modern businesses. By understanding the fundamentals, you can better appreciate the need for effective solutions.
- Shaytards Youtube
- Blameitonkway Restaurant
- David Dobrik Net Worth 2023
- Youtube Della Vlogs
- Jackson Myles Net Worth
IoT Device Categories
- Consumer IoT: Smart home devices, wearables, and personal gadgets.
- Enterprise IoT: Industrial equipment, healthcare devices, and smart infrastructure.
- Industrial IoT: Machinery, robotics, and automation systems.
Understanding Firewalls
Firewalls are security systems designed to monitor and control incoming and outgoing network traffic. They act as a barrier between internal and external networks, preventing unauthorized access while allowing legitimate connections. Firewalls can be hardware-based, software-based, or a combination of both.
When it comes to IoT devices, firewalls play a crucial role in protecting sensitive data and preventing cyberattacks. However, they can also complicate remote access by blocking external connections. Understanding how firewalls work is essential for finding effective solutions to this problem.
Types of Firewalls
- Packet Filtering Firewalls: Basic firewalls that filter traffic based on IP addresses and port numbers.
- Stateful Inspection Firewalls: Advanced firewalls that track the state of active connections.
- Application-Level Gateways: Firewalls that inspect and filter traffic at the application layer.
Why Use Mac Server
Mac servers offer a robust and user-friendly platform for managing IoT devices. Powered by macOS, these servers provide advanced security features, seamless integration with other Apple devices, and a wide range of tools for network management. Using a Mac server for remote IoT access ensures a secure and efficient environment for managing connected devices.
Some of the key advantages of using a Mac server include:
- Strong security protocols.
- Easy setup and configuration.
- Compatibility with various IoT platforms.
Methods to Access IoT Devices
There are several methods to access IoT devices behind firewalls using a Mac server. Each method has its own advantages and limitations, making it essential to choose the right solution based on your specific needs.
Common Methods
- VPN Solutions
- Port Forwarding
- Reverse SSH Tunnel
- Cloud-Based Solutions
VPN Solutions
A Virtual Private Network (VPN) creates a secure connection between two networks, allowing you to access IoT devices behind firewalls. By encrypting data and routing it through a secure tunnel, VPNs provide a safe way to manage remote devices without compromising security.
Setting up a VPN on a Mac server involves configuring the server as a VPN endpoint and establishing client connections from remote locations. Popular VPN protocols include OpenVPN, IPSec, and L2TP.
Benefits of Using a VPN
- Enhanced security through encryption.
- Seamless access to IoT devices.
- Compatibility with multiple devices and platforms.
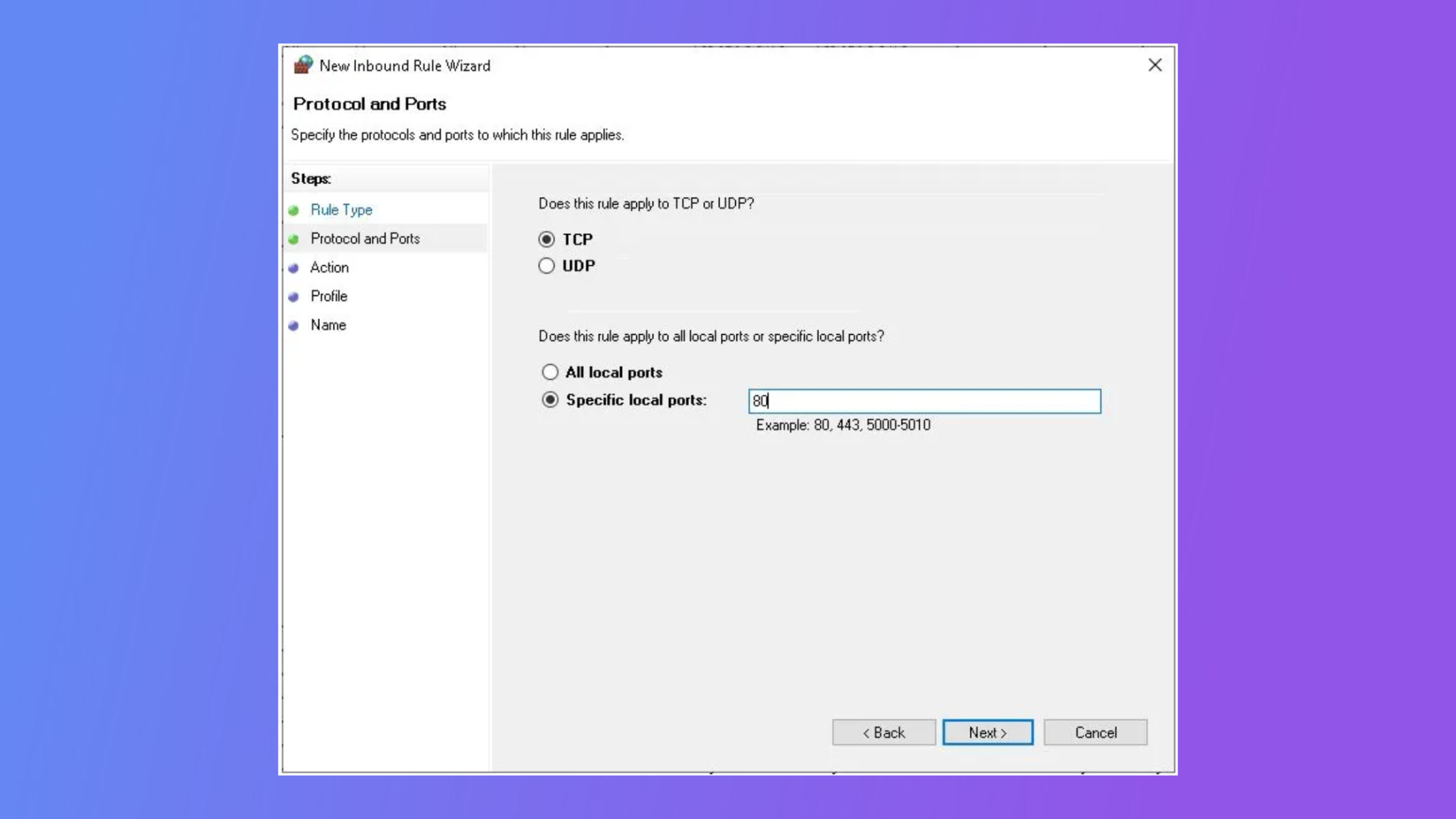
Port Forwarding
Port forwarding is a technique used to redirect network traffic from one port to another, allowing external devices to access IoT devices behind firewalls. By configuring port forwarding on your router, you can create a direct connection to specific devices on your network.
While port forwarding is a simple and effective solution, it requires careful configuration to ensure security. Exposing ports to the internet can increase the risk of cyberattacks, so it's essential to use strong passwords and firewalls to protect your network.
Steps to Configure Port Forwarding
- Identify the IP address of the IoT device.
- Log in to your router's admin panel.
- Set up port forwarding rules for the desired ports.
Reverse SSH Tunnel
A reverse SSH tunnel allows you to securely connect to IoT devices behind firewalls by creating a tunnel from the remote device to the Mac server. This method is particularly useful when the IoT device has limited outbound connectivity but can initiate connections to external servers.
To set up a reverse SSH tunnel, you need to configure the IoT device to connect to the Mac server using SSH. Once the tunnel is established, you can access the device remotely through the server.
Advantages of Reverse SSH Tunnel
- Secure and encrypted connections.
- Minimal configuration required on the firewall.
- Works with limited outbound connectivity.
Cloud-Based Solutions
Cloud-based solutions offer a scalable and flexible way to manage IoT devices remotely. By hosting IoT data and applications in the cloud, you can access devices from anywhere without worrying about firewall restrictions. Cloud platforms like AWS IoT, Google Cloud IoT, and Azure IoT provide robust tools for managing connected devices.
Integrating a Mac server with cloud-based solutions allows you to leverage the power of cloud computing while maintaining control over your network. This approach is ideal for businesses that require high availability and scalability.
Key Features of Cloud-Based Solutions
- Scalability and flexibility.
- Real-time data processing and analytics.
- Seamless integration with existing systems.
Security Considerations
When accessing IoT devices behind firewalls, security should always be a top priority. Cyber threats such as hacking, data breaches, and malware can compromise your network and sensitive information. Implementing robust security measures is essential to protect your IoT infrastructure.
Some best practices for securing IoT devices include:
- Using strong passwords and multi-factor authentication.
- Regularly updating firmware and software.
- Implementing firewalls and intrusion detection systems.
Best Practices
To ensure successful remote IoT management using a Mac server, follow these best practices:
- Choose the right method based on your specific needs and network configuration.
- Regularly monitor and audit your network for potential security vulnerabilities.
- Document your setup and configuration for future reference.
Conclusion
Managing remote IoT devices behind firewalls using a Mac server is a complex but achievable task. By understanding the basics of IoT, firewalls, and Mac servers, you can implement effective solutions to overcome these challenges. Whether you choose VPNs, port forwarding, reverse SSH tunnels, or cloud-based solutions, ensuring security and reliability should always be your top priority.
We encourage you to share your thoughts and experiences in the comments section below. Additionally, feel free to explore other articles on our website for more insights into IoT and network management. Together, we can build a safer and more connected world.
- Vice Grip Garage Apparel
- How Many Subscribers Do The Stokes Twins Have
- Damian And Deion
- Sugarstar Age
- Rio Da Yung Og Prison

Monitor IoT Behind Firewall A Guide for Robust Security

How To Use RemoteIoT Behind Firewall Using Mac A Comprehensive Guide
How To Use RemoteIoT Behind Firewall Using Mac A Comprehensive Guide