Mastering SSH Remote Access Device: A Comprehensive Guide For Secure Connections
SSH remote access device has become an essential tool for IT professionals and system administrators around the world. It allows secure communication between devices over unsecured networks, ensuring data integrity and confidentiality. Whether you're managing servers remotely or accessing sensitive files from a distant location, understanding SSH is crucial for maintaining robust cybersecurity practices.
As remote work continues to grow in popularity, the demand for secure methods of accessing devices remotely has surged. This guide will delve into everything you need to know about SSH remote access devices, exploring its features, benefits, and best practices. By the end of this article, you'll have a solid foundation to implement SSH effectively in your workflow.
From setting up SSH connections to troubleshooting common issues, we'll cover all aspects of SSH remote access devices. Whether you're a beginner looking to understand the basics or an experienced professional seeking advanced tips, this article is designed to cater to your needs. Let's dive in!
- Kaytranada Net Worth
- What If Kevin Macleod Copyright His Music
- Lucas Cruikshank Brother
- Sos Vs Bro
- Authenticteecee
Table of Contents
- What is SSH?
- Benefits of Using SSH
- How SSH Works
- Setting Up SSH
- Securing SSH Connections
- Common SSH Commands
- Troubleshooting SSH Issues
- Best Practices for SSH Remote Access
- Alternatives to SSH
- The Future of SSH
What is SSH?
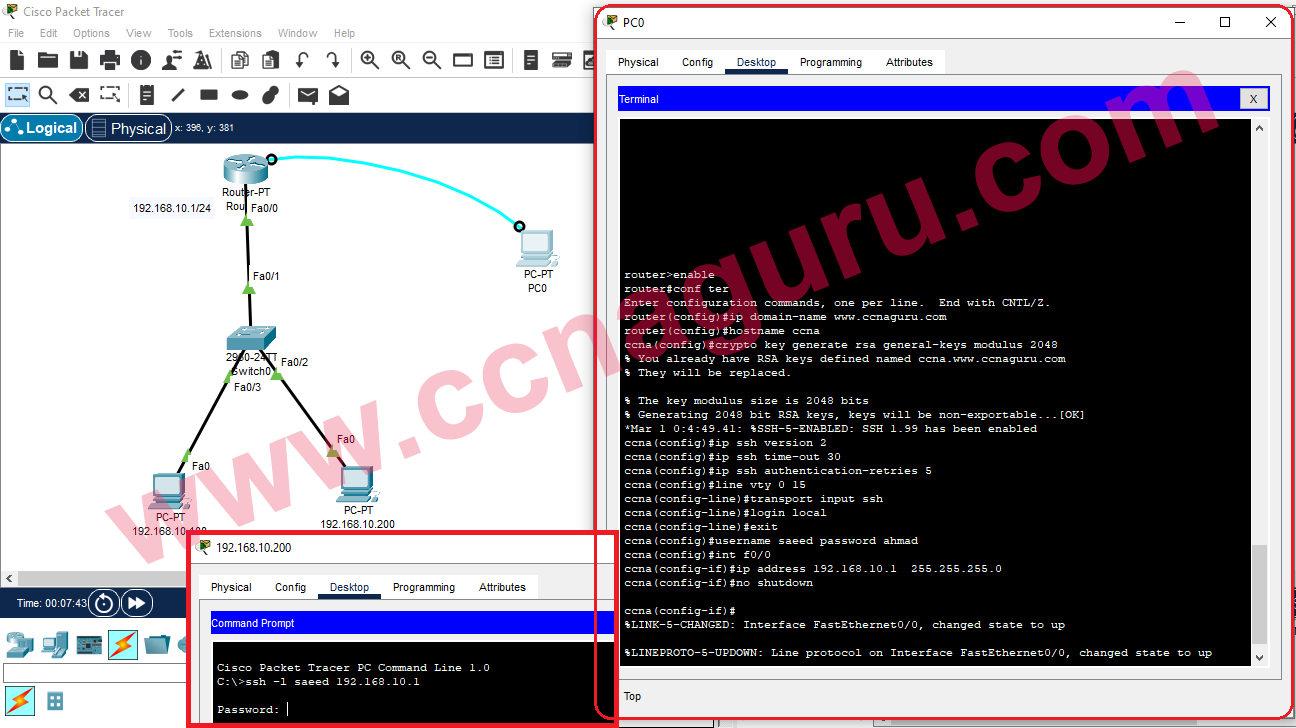
SSH, or Secure Shell, is a cryptographic network protocol used for secure data communication over untrusted networks. It provides a secure way to access remote devices, transfer files, and execute commands on remote systems. SSH remote access device ensures that sensitive information, such as passwords and private keys, remains encrypted during transmission.
Key Features of SSH
SSH offers several key features that make it indispensable for modern IT operations:
- Encryption: SSH encrypts all data transmitted between devices, ensuring confidentiality.
- Authentication: It supports various authentication methods, including password-based and public-key authentication.
- Port Forwarding: SSH allows for secure tunneling of other protocols, such as HTTP and FTP.
- File Transfer: The SSH File Transfer Protocol (SFTP) enables secure file transfers over SSH connections.
Benefits of Using SSH
Adopting SSH remote access device brings numerous advantages to organizations and individuals alike. Below are some of the most significant benefits:
Enhanced Security
SSH protects against common cybersecurity threats, such as man-in-the-middle attacks and eavesdropping. Its robust encryption algorithms ensure that sensitive data remains secure during transmission.
Efficiency and Convenience
With SSH, users can manage multiple remote devices from a single workstation. This streamlines IT operations and reduces the need for physical access to devices.
Wide Compatibility
SSH is compatible with a wide range of operating systems, including Linux, macOS, and Windows. This makes it a versatile tool for cross-platform environments.
How SSH Works
SSH operates on a client-server model, where the client initiates the connection and the server authenticates the client before establishing a secure session. Here's a step-by-step breakdown of how SSH works:
Step 1: Connection Initiation
The client sends a request to the server to establish an SSH connection. The server responds with its public key, which the client uses to verify the server's identity.
Step 2: Authentication
Once the connection is established, the client must authenticate itself to the server. This can be done using passwords, public keys, or other authentication methods.
Step 3: Encrypted Communication
After successful authentication, both parties agree on encryption algorithms and keys to secure the communication channel. All subsequent data exchanged between the client and server is encrypted.
Setting Up SSH
Setting up SSH remote access device involves configuring both the client and server components. Below are the steps to set up SSH on different operating systems:
Setting Up SSH on Linux
Most Linux distributions come with SSH pre-installed. To enable SSH server functionality, you need to install and configure the OpenSSH server package. Use the following commands:
- Install OpenSSH:
sudo apt-get install openssh-server - Start the SSH service:
sudo service ssh start - Configure SSH settings in
/etc/ssh/sshd_config
Setting Up SSH on Windows
Windows 10 and later versions support SSH natively. To enable SSH, follow these steps:
- Open "Turn Windows features on or off" and enable "OpenSSH Server."
- Restart your computer to apply the changes.
- Configure SSH settings in
C:\ProgramData\ssh\sshd_config.
Securing SSH Connections
While SSH provides strong security by default, additional measures can further enhance its protection. Here are some best practices for securing SSH connections:
Disable Password Authentication
Switch to public-key authentication to eliminate the risk of brute-force password attacks. Update the sshd_config file to include:
PasswordAuthentication no
Use Strong Key Pairs
Generate strong RSA or ED25519 key pairs for public-key authentication. Avoid using weak or default keys.
Limit User Access
Restrict SSH access to specific users or groups by modifying the sshd_config file:
AllowUsers user1 user2
Common SSH Commands
Here are some essential SSH commands that every user should know:
Connecting to a Remote Server
Use the following command to connect to a remote server:
ssh username@remote_host
Copying Files with SCP
Transfer files securely using the SCP command:
scp local_file username@remote_host:remote_path
Using SFTP for File Management
SFTP allows for interactive file management over SSH:
sftp username@remote_host
Troubleshooting SSH Issues
Despite its reliability, SSH connections can sometimes encounter issues. Here are some common problems and their solutions:
Connection Refused
This error typically occurs when the SSH service is not running on the server. Ensure the SSH service is active and listening on the correct port.
Permission Denied (Public Key)
This issue arises when the client's public key is not authorized on the server. Verify that the public key is correctly added to the server's authorized_keys file.
Best Practices for SSH Remote Access
To maximize the security and efficiency of SSH remote access device, follow these best practices:
Regularly Update SSH Software
Keep your SSH client and server software up to date to protect against known vulnerabilities.
Monitor SSH Logs
Regularly review SSH logs to detect and respond to suspicious activities.
Implement Two-Factor Authentication
Add an extra layer of security by enabling two-factor authentication for SSH connections.
Alternatives to SSH
While SSH is the most widely used protocol for remote access, there are alternative solutions available:
RDP (Remote Desktop Protocol)
RDP is commonly used for remote access to Windows systems and provides a graphical interface for managing remote devices.
TELNET
Although less secure than SSH, TELNET is still used in some legacy systems for remote access.
The Future of SSH
As cybersecurity threats continue to evolve, the development of SSH will focus on enhancing its security features and improving usability. Future versions may incorporate advanced encryption algorithms and more robust authentication mechanisms.
Adoption of Quantum-Resistant Algorithms
With the rise of quantum computing, SSH may adopt quantum-resistant algorithms to ensure long-term security.
Integration with Cloud Services
SSH is likely to become more integrated with cloud platforms, enabling seamless remote access to cloud-based resources.
Kesimpulan
SSH remote access device is a powerful tool for secure communication and remote management. By understanding its features, benefits, and best practices, you can leverage SSH to enhance your cybersecurity posture and streamline IT operations. Remember to follow the guidelines outlined in this article to ensure secure and efficient SSH usage.
Take action today by implementing SSH in your workflow and sharing this article with others who may benefit from it. For more insights and tips, explore our other articles on cybersecurity and IT solutions.

SSH for Remote Access Every User, Every Device, Every Application

CDA Remote access device
Securing Remote Access to a Cisco Router Using SSH « CCNA Online